Netcat
- EN
- PT
Table of Contents
I heard too many times a work colleague, or a third-party vendor telling me “there is something wrong on the network here”, or “This port isn’t open!”.
You can use websites to try to test for open ports, a quick Google search should yield you a couple good results, but sometimes that is not enough.
#
The problem
Let’s suppose you followed my other post about restricting source address with iptables, in this case those random web tools won’t help you, so you use nmap!
I will make a post about nmap in the future, for now let’s use it in a very simple way to check for an open port:
$ sudo nmap -sS -p 80 example.com
Password:
Starting Nmap 7.95 ( https://nmap.org ) at 2024-10-31 22:08 -03
Nmap scan report for example.com (192.0.0.4)
Host is up (0.18s latency).
Other addresses for example.com (not scanned): 2001:db8::192:0:0:4
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.39 seconds
As you can see, the important part is -p 80, which specifies that we want to test port 80, and the last argument is the host we are scanning.
Now let’s suppose that another person which is setting up a PABX, which is a classical example… I have a lot of histories about telephony people… For example, he may have set a simple wrong configuration, like the gateway or subnet mask, and that causes his service to not work. He does the same tests I showed above, but instead of “open” that says the port is “filtered”.
That is enough argument for him, now he will blame your network for that. How can we prove that our firewall rules are correct and working?
The simplest answer is using netcat!
#
netcat (nc)
Netcat is a very simple, but very powerful tool for those cases. With that, you can setup a listener on any TCP or UDP port!
##
Installing
The installation is very simple! On Debian systems you can do it with the command:
sudo apt install netcat
##
Using the tool
I invite you to read the nc man page.
The main options we need to use are:
- -p : This specifies which port should we listen to.
- -k : This makes netcat to keep listening after a client disconnects.
- -u : Use UDP instead of TCP
##
Use cases
###
Check for network communication
Listen on port 2000:
nc -l 2000
This starts a server which listens on port 2000.
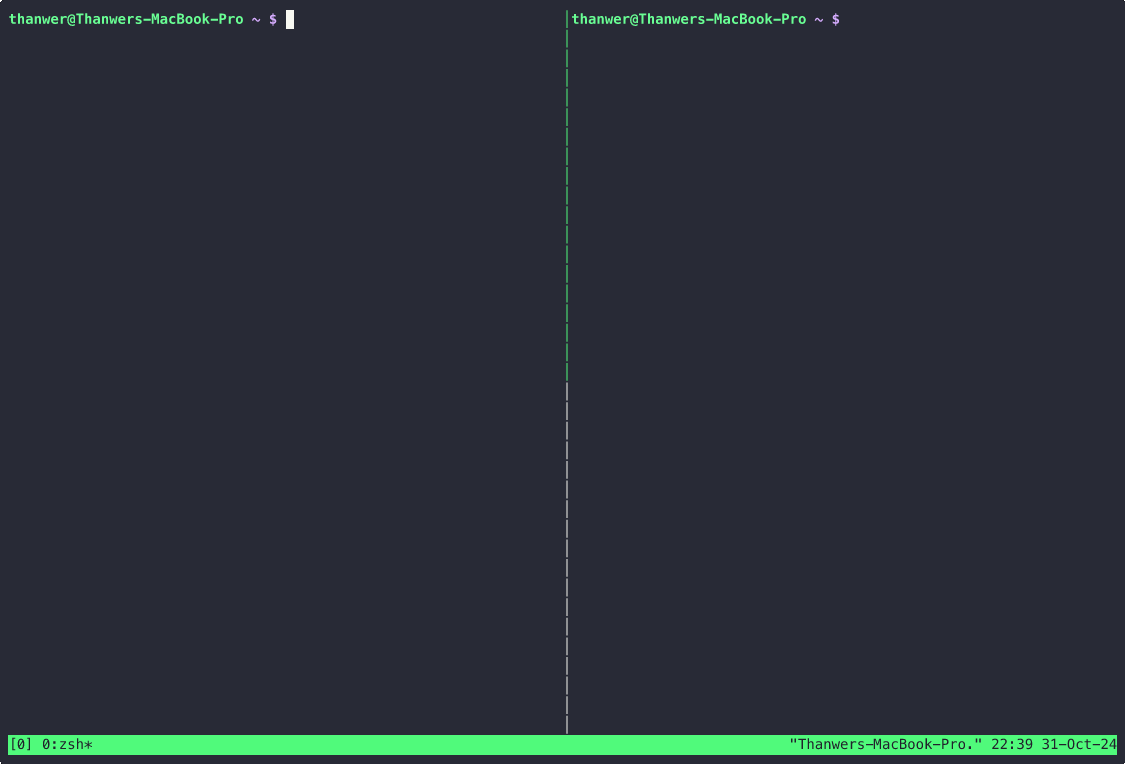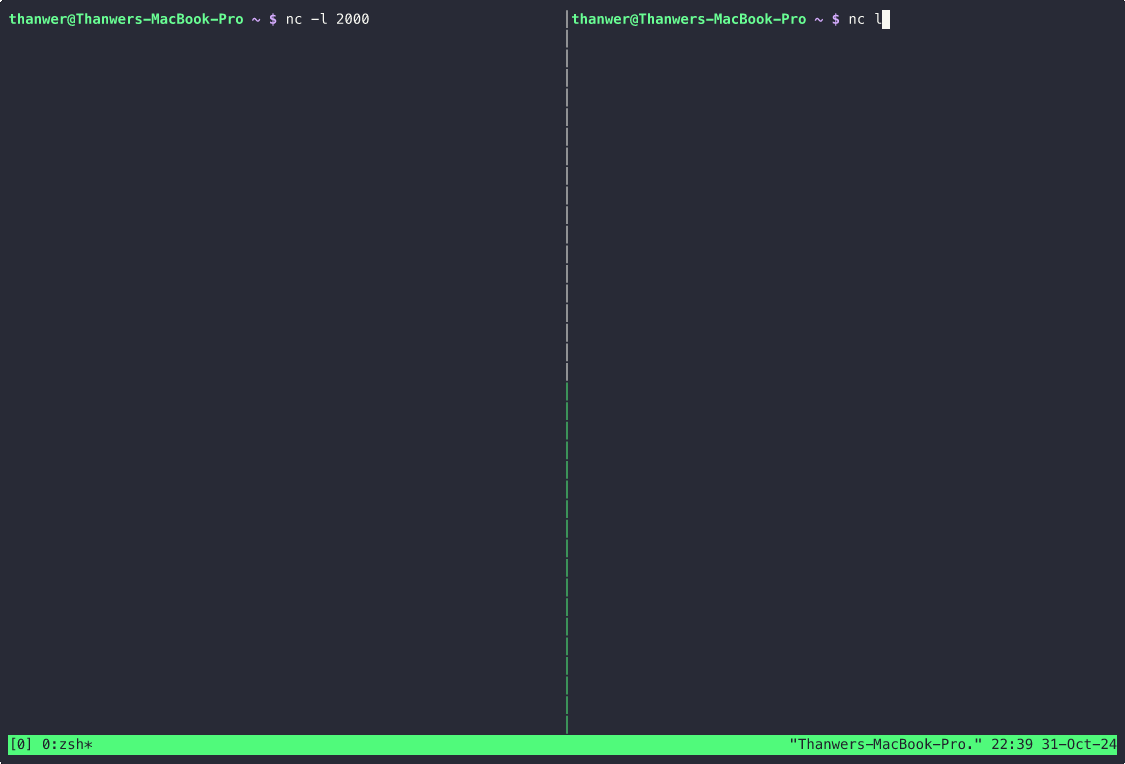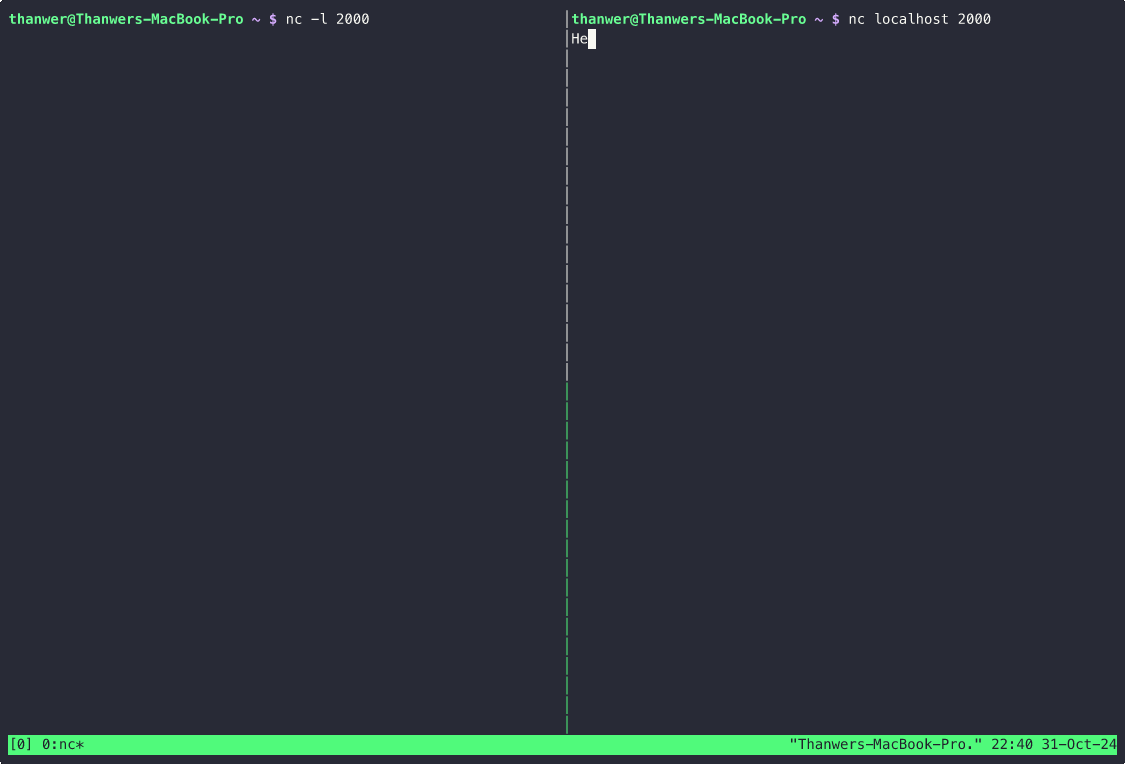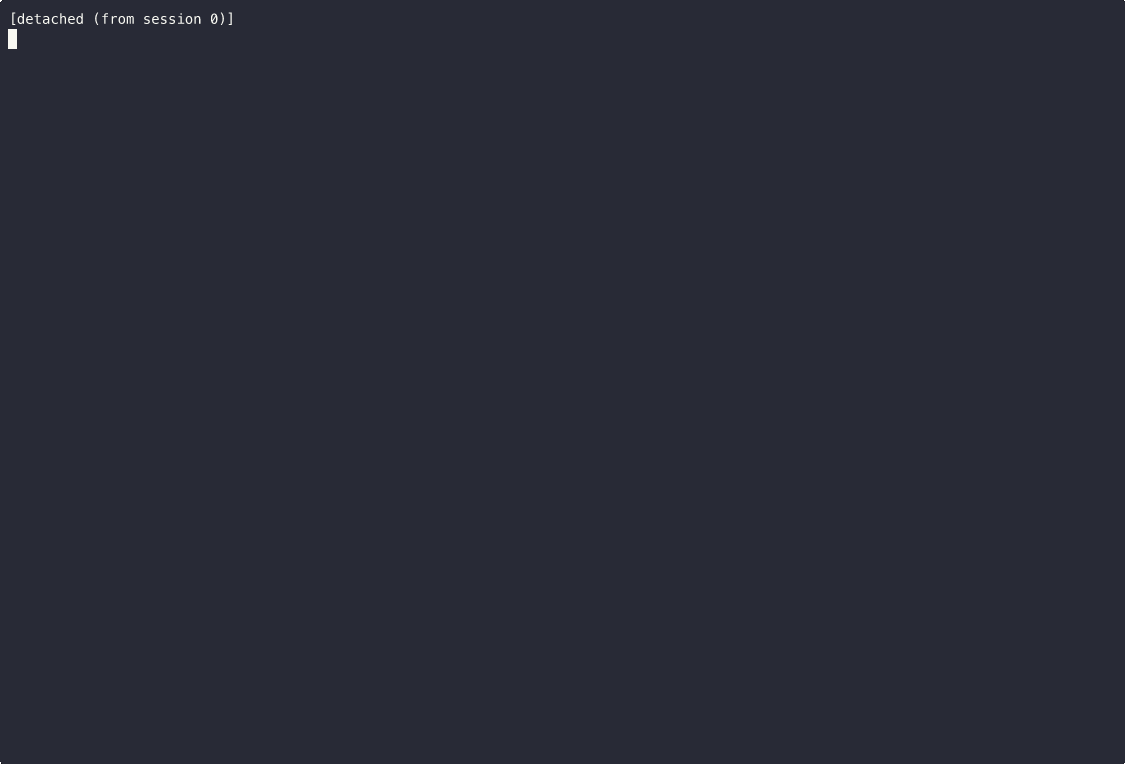
Now let’s open another terminal and connect a client to this port:
nc localhost 2000
On both terminals you should see as a chat app working, this is being transmitted over the network!
See an example of this working:
###
File transfer
Netcat can be used to send and receive files between two hosts over a network. This can be particularly useful in environments without FTP or SCP access.
On the receiver’s end:
nc -l -p 1234 > received_file.txt
On the sender’s end, assuming that 192.0.0.2 is the receiving server:
nc 192.0.0.2 -p 1234 < file_to_send.txt
This can be useful for transferring a log file for example.
###
Port scan
nc can be used as a simpler alternative to nmap:
$ nc -z host.example.com 20-30
Connection to host.example.com 22 port [tcp/ssh] succeeded!
Connection to host.example.com 25 port [tcp/smtp] succeeded!
###
Directly talking to servers
nc can be used as an alternative to telnet for troubleshooting.
For example, you can talk to a SMTP server directly over port 25:
$ nc localhost 25 << EOF
HELO host.example.com
MAIL FROM: <user@host.example.com>
RCPT TO: <user2@host.example.com>
DATA
Body of email.
.
QUIT
EOF